

 Research
|
Projects
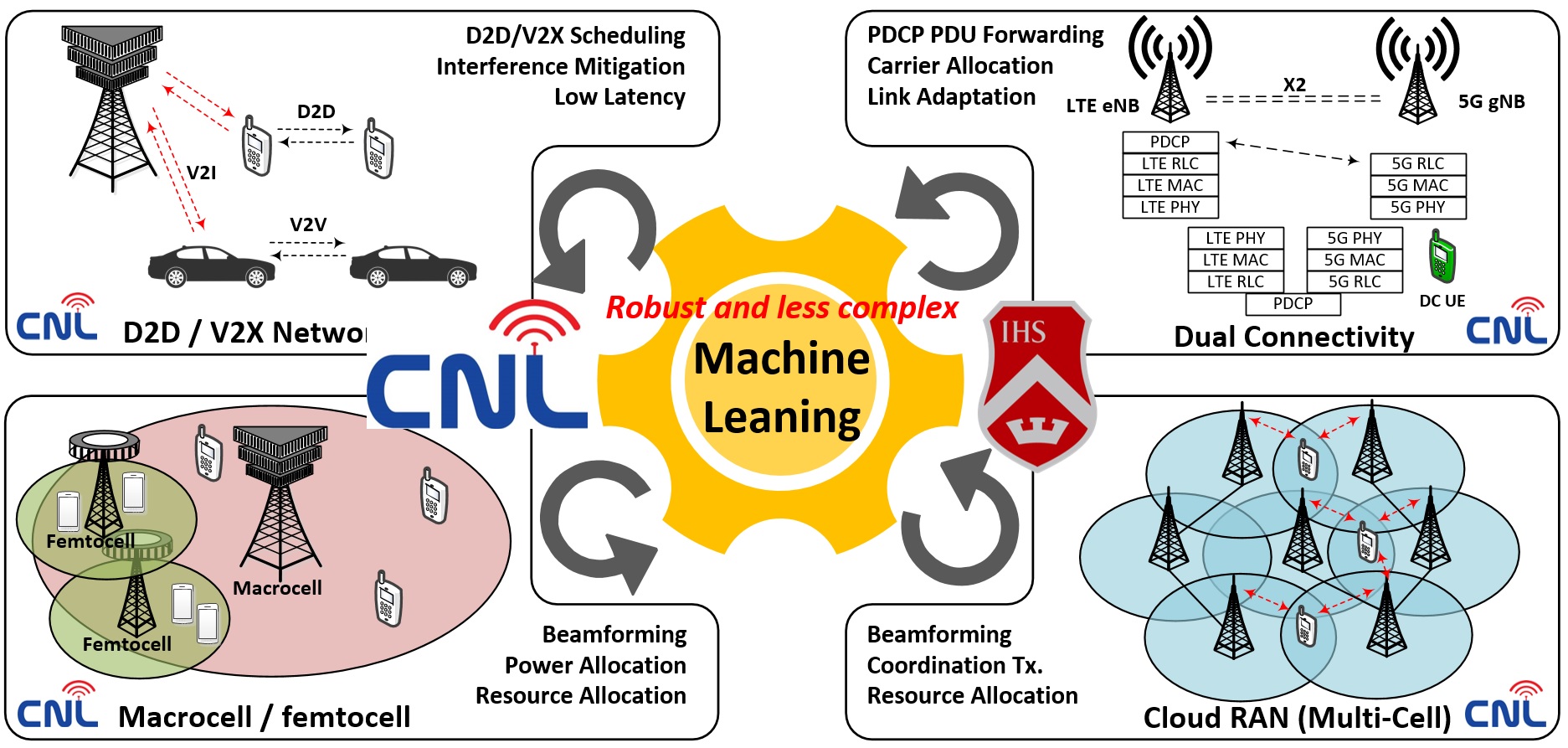
CNL (Communications and Networking Laboratory) covers AI/ML technologies, Connectivity protocols, and Security for 5G/6G, IoT, and Vehicle networks.
Research topics are
Research
|
Projects
CNL (Communications and Networking Laboratory) covers AI/ML technologies, Connectivity protocols, and Security for 5G/6G, IoT, and Vehicle networks.
Research topics are
| Wireless AI - AI/ML Empowered 5G/6G, Connected Car, and IoT |
|
Artificial Intelligence (AI)-RAN for 6G:
AI, which learns from the perceived environment and can exploit the increasingly massive datasets available from wireless systems, can be used to solve complex and previously intractable problems. Many problems in wireless communication systems, such as decision making, resource optimization, and network management, can be cast in a form that is suitable to be solved by AI techniques. Hence, AI technologies have been applied to improve the performance of future wireless communication systems.
We focus on the design of AI/ML empowered PHY, MAC, and network layers for 6G.
Deep Learning (DL) for CSI feedback, Beam Management, and RRM:
Resource management problems in systems and networking often manifest as difficult online decision making tasks where appropriate solutions depend on understanding the workload and environment. We apply recent DL technologies to wireless networks.
Deep Reinforcement Learning (DRL) for Wireless Networks:
The integration of DRL into future wireless networks will revolutionize the conventional model-based network optimization to model-free approaches and meet various application demands. By interacting with the environment, DRL provides an autonomous decision-making mechanism for the network entities to solve non-convex, complex model-free problems, e.g., spectrum access, handover, scheduling, caching, data offloading, and resource allocation.
Constrained Reinforcement Learning (CRL) for AI-RAN:
Learning can transform sysem engineering practice by automating the engineering design cycle. But it can do so only if we incorporate requirements in the practice of machine learning.
Safety is one of the bottlenecks hindering the use of RL in real-world applications such as URLLC services, physical robotics, healthcare, and autonomous driving.
Recently, safety has become a major research concern in AI-RAN applications. However, when it comes to multi-agent systems, a great challenge is exacerbated by policy conflicts caused by multiple agents interacting within a shared environment and learning simultaneously.
In other words, each agent must not only satisfy its own safety constraints, but also consider conflicts between its safety constraints and reward maximization, as well as the safety constraints of other agents, to ensure the safety of their collective actions.
 |
|
| AI empowered 6G | |
 |
 |
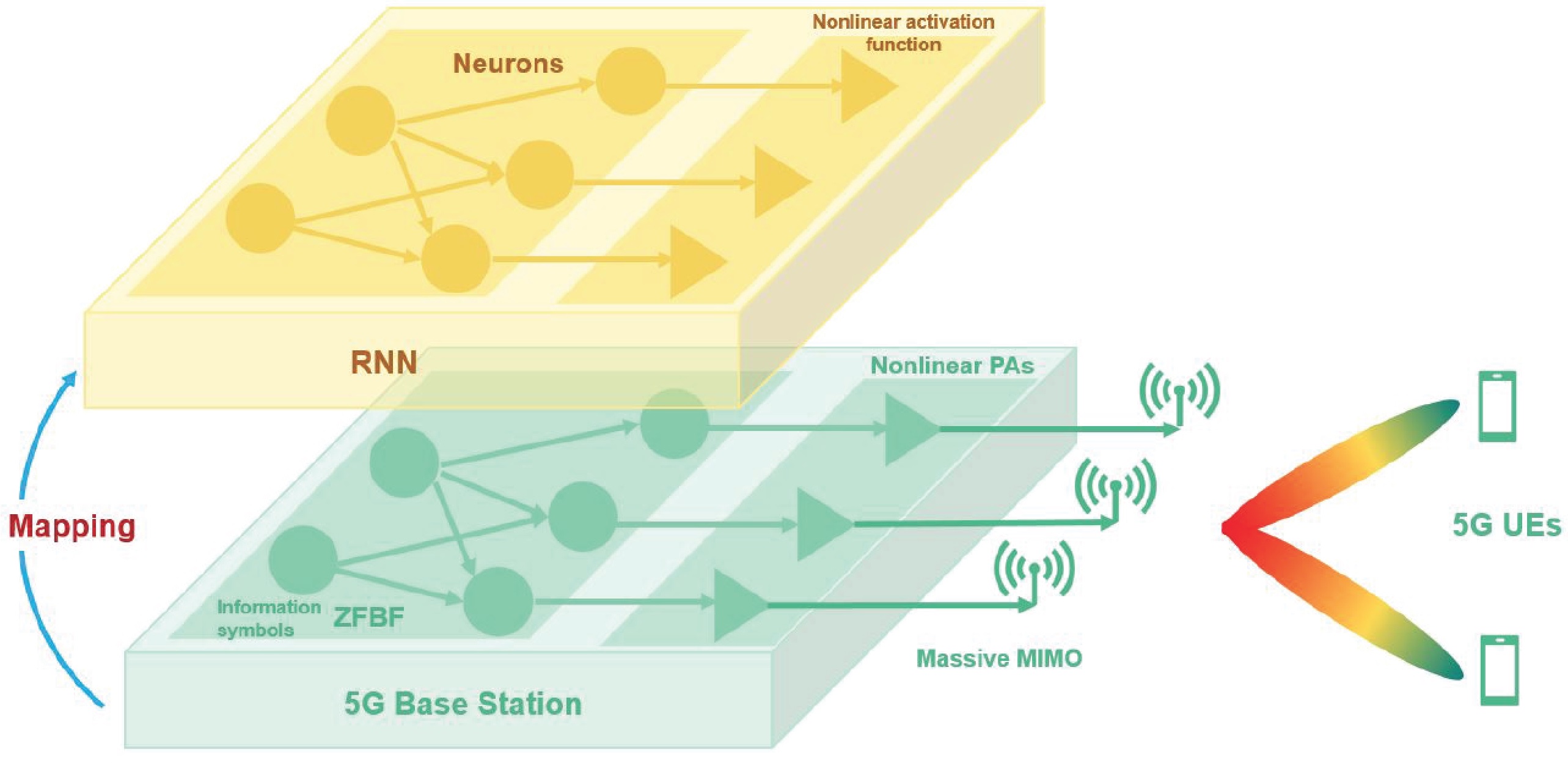
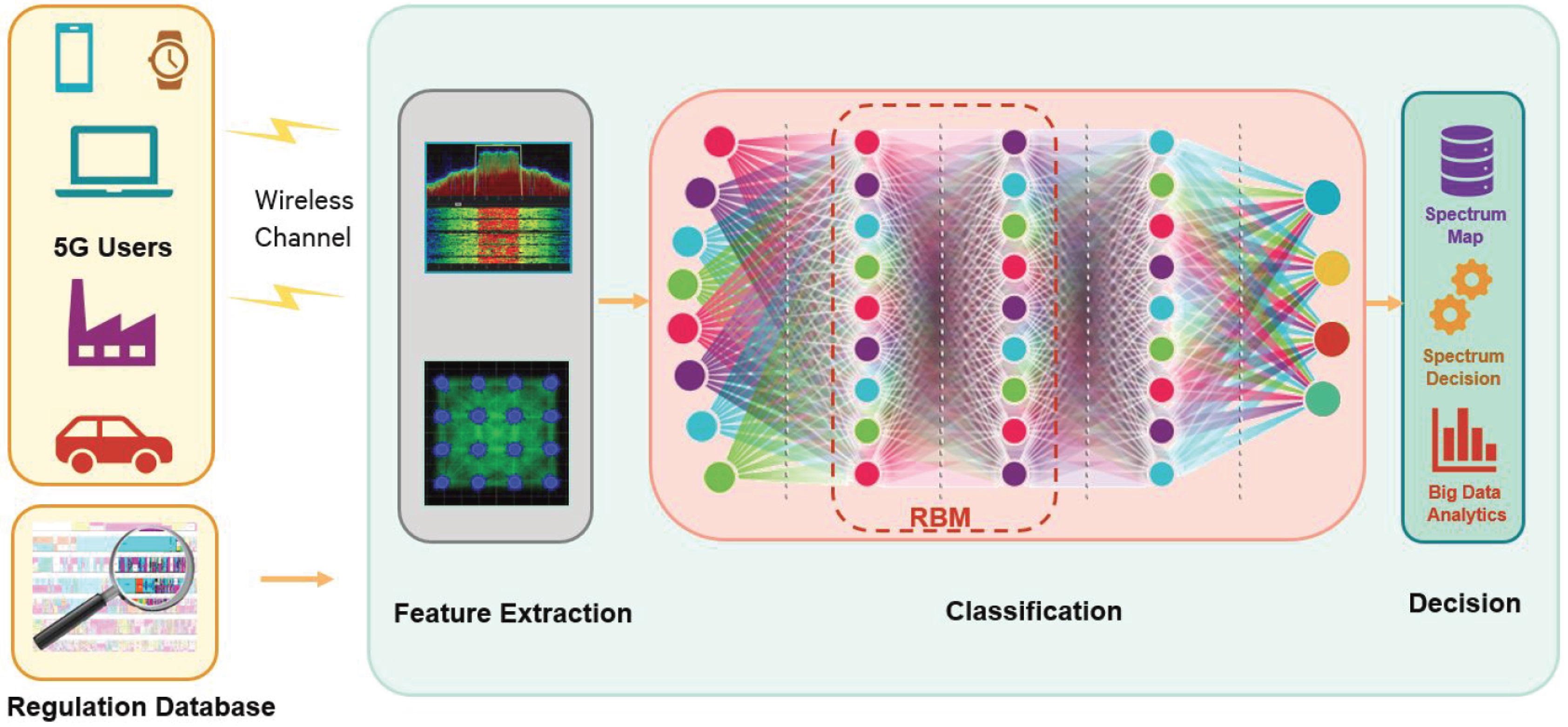
| RNN-based Solution for 5G Massive MIMO | Reconfigurable Deep Learning Framework for AI-aided 5G BS Systems |
 |
 |
| CNL's Machine Learning for Wireless Networks | CNL's Machine Learning Simulator (ongoing) |
| Wireless Connectivity - Radio access technologies for 5G/6G, V2X, and IoT |
|
Integrated Sensing And Communication (ISAC) ISAC refers to the design paradigm and corresponding enabling technologies that combine sensing and communication systems to utilize resources efficiently and even to pursue mutual benefits.
ISAC can acquire two main advantages over dedicated sensing and communication functionalities: 1) Integration gain to efficiently utilize congested resources for dual use of both communications and sensing, and even more interesting, 2) Coordination gain to balance dual-functional performance or/and perform mutual assistance.
ISAC has been recently identified as an enabling technology for B5G/6G.
Applications of ISAC have been extended to numerous emerging areas, including vehicular networks, environmental monitoring, Internet of Things, as well as in-door services such as human activity recognition.
Cellular Connectivity cover architectures and protocols for 5G/6G wiereless communications and networking. Research topics are learning-based radio resource management, NR technologies for 5G and beyond, multiple-input multiple-output (MIMO), device-to-device communications, etc.
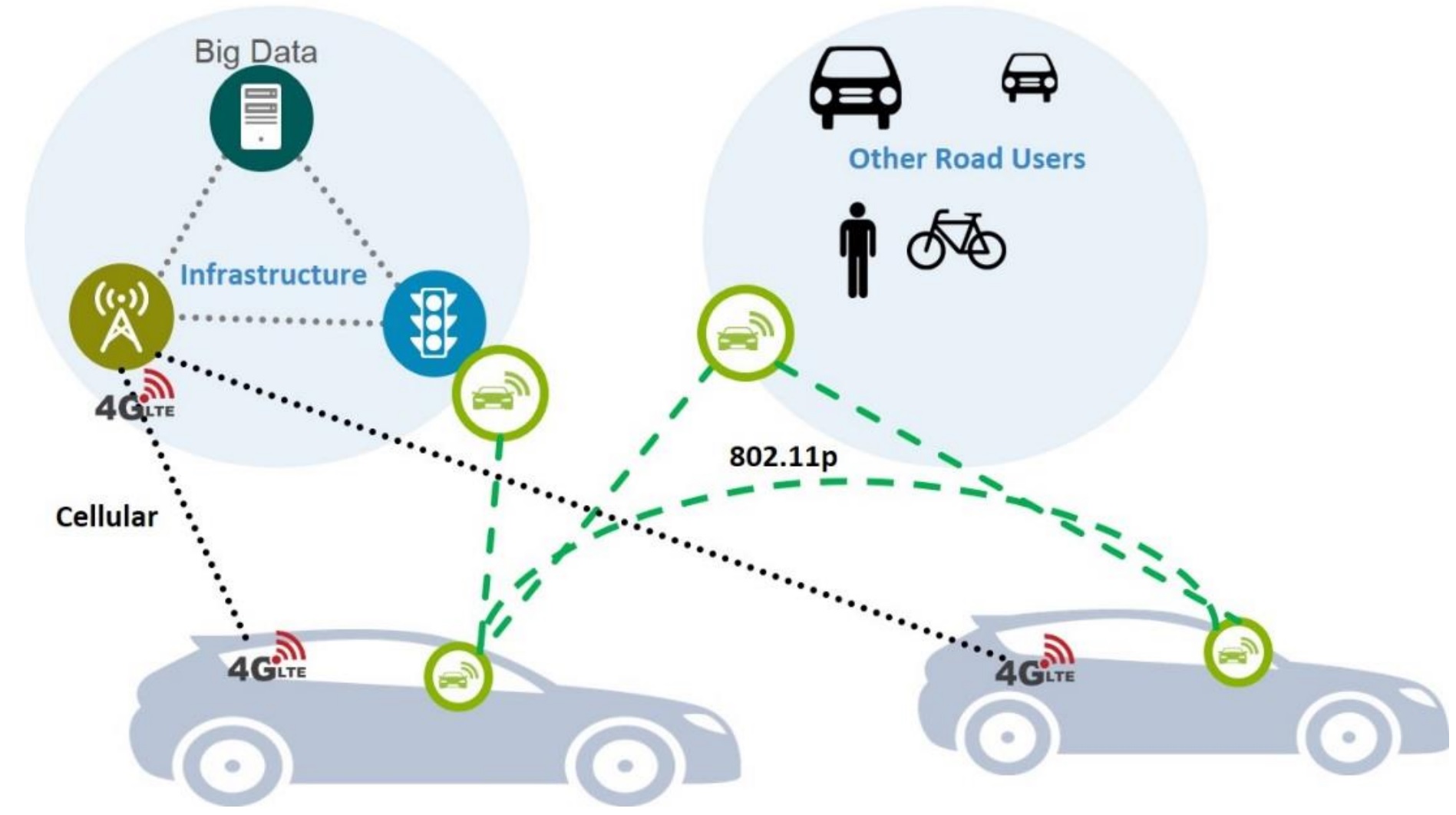
Vehicle-to-everything (V2X) Connectivity:
C-V2X is a growing area of communications between vehicles and including roadside communication infrastructure. Advances in wireless communications are making possible sharing of information through real time communications between vehicles and infrastructure. This has led to applications to increase safety of vehicles and communication between passengers and the Internet.
Additionally, 3GPP Rel. 16 introduces 5G NR V2X communications including sidelink (SL) communications. NR V2X SL is to support enhanced V2X (eV2X) use cases related to connected and automated driving.
Research topics are cellular-V2X and WAVE-based V2X (C-ITS) for autonomous driving and cooperative adaptive cruise control (CACC); and massive BDMA and radio resource management for vehicle communications.
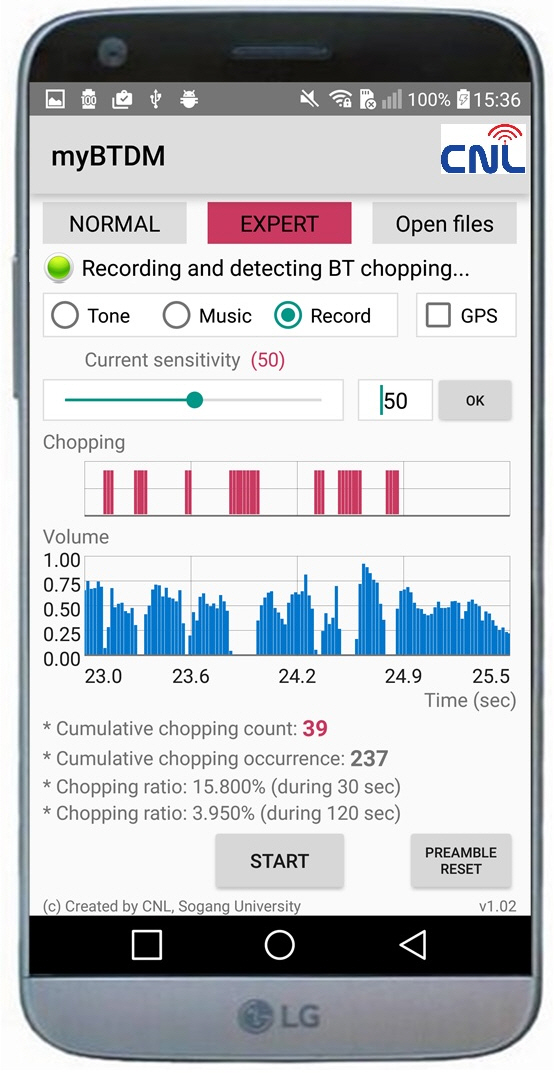
IoT Connectivity cover NB-IoT, LoRa, Wi-Fi, and Bluetooth. Research topics are response time and energy efficiency of IoT devices discovery; wireless access and communications technologies; conectivity and clustering; network platforms; coexistance of BT/Wi-Fi in the crowded 2.4GHz networks; and qalfication and improvement of audio chooping over bluetooth A2DP.
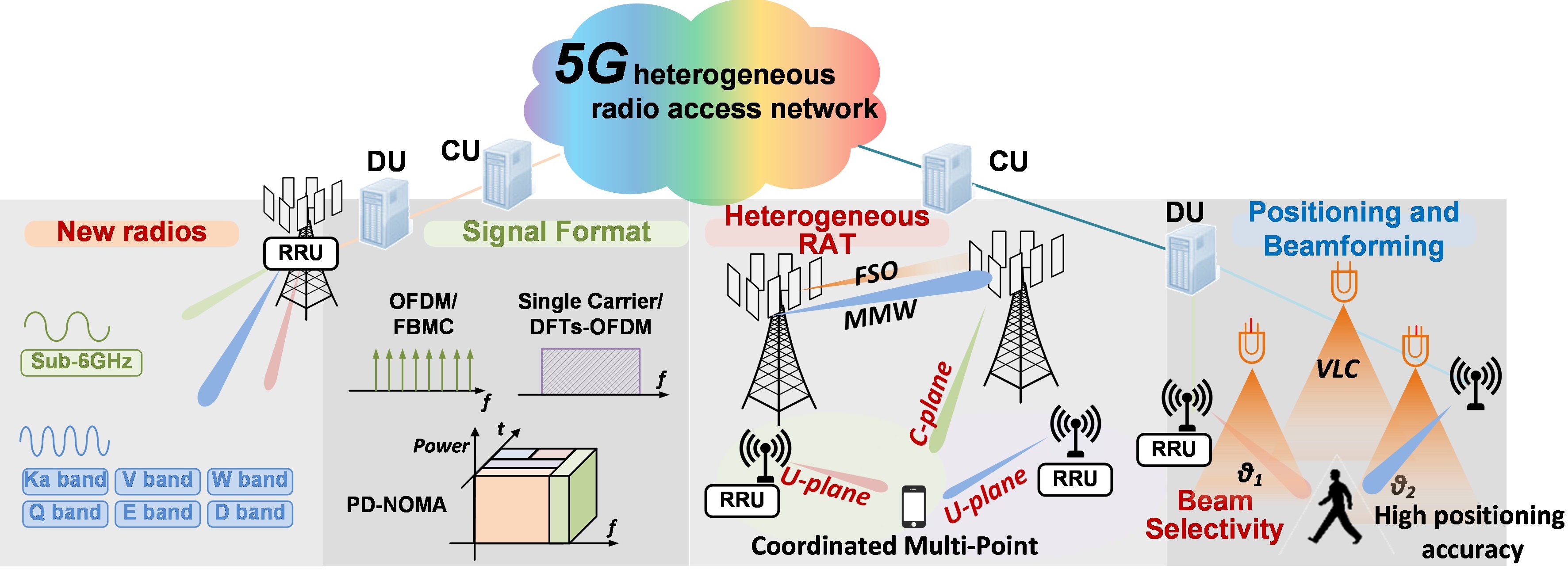 |
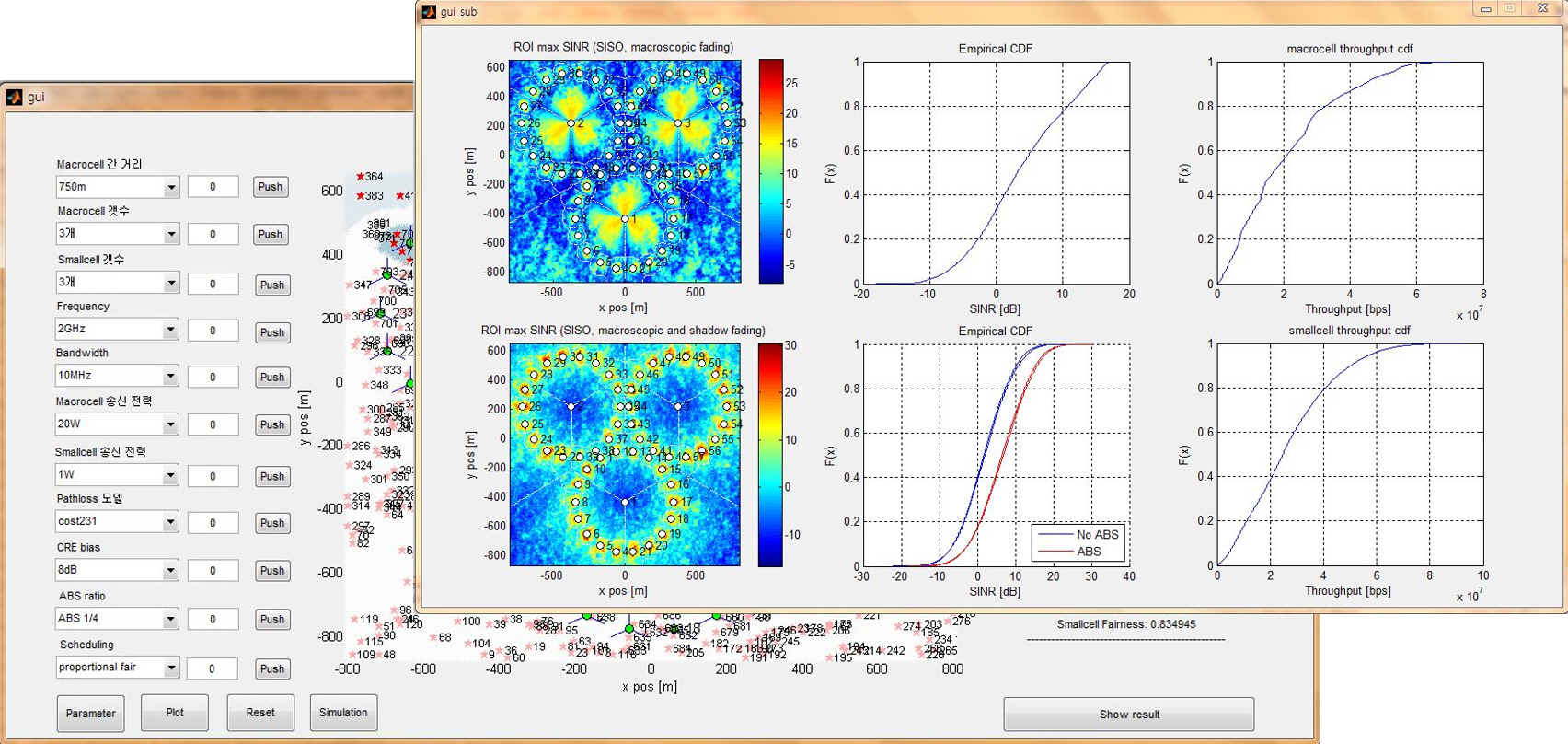 | ||
| 5G Radio Access Technologies | LTE/5G Simulator developed by CNL | ||
 |
 |
 |
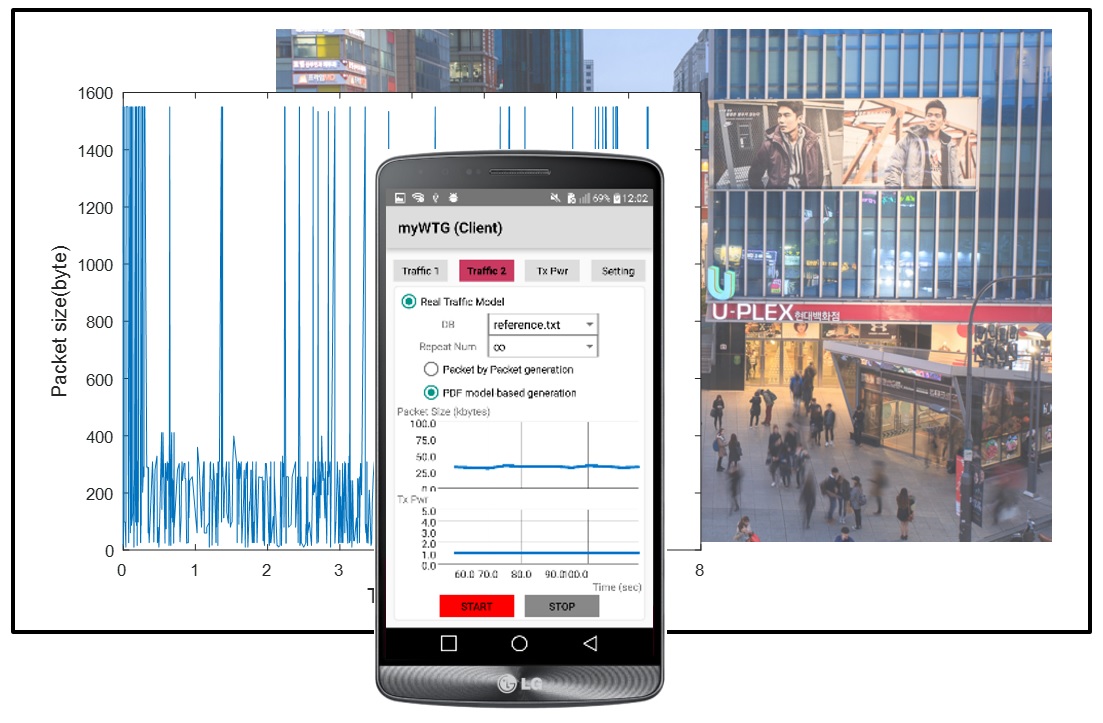 |
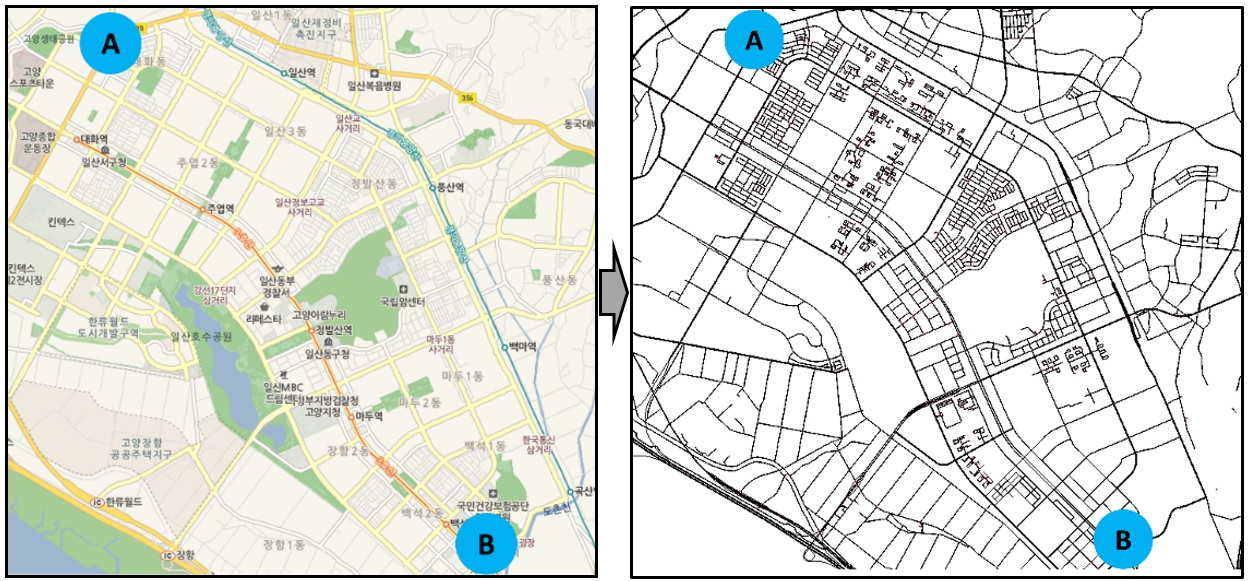
| Celluar-V2X and WAVE-V2X | SUMO-based Autonomous Driving Connectivity developed by CNL |
BT DM App developed by CNL |
Real Wi-Fi Traffic Generator App developed by CNL |
| Wireless Security - Security issues in Celluar, Connected Car, IoT, and Blockchain |
|
Wireless Security covers securitiy issues in the wireless communications, e.g., LTE/LTE-A, 5G/6G, Bluetooth, Smart Home Remote Control, Wi-Fi, etc.
LTE/5G is assumed to guarantee confidentiality and strong authentication. However, LTE/5G networks are vulnerable to wireless security. We study on the insecurity rationale behind celluar protocol exploits and rogue base stations.
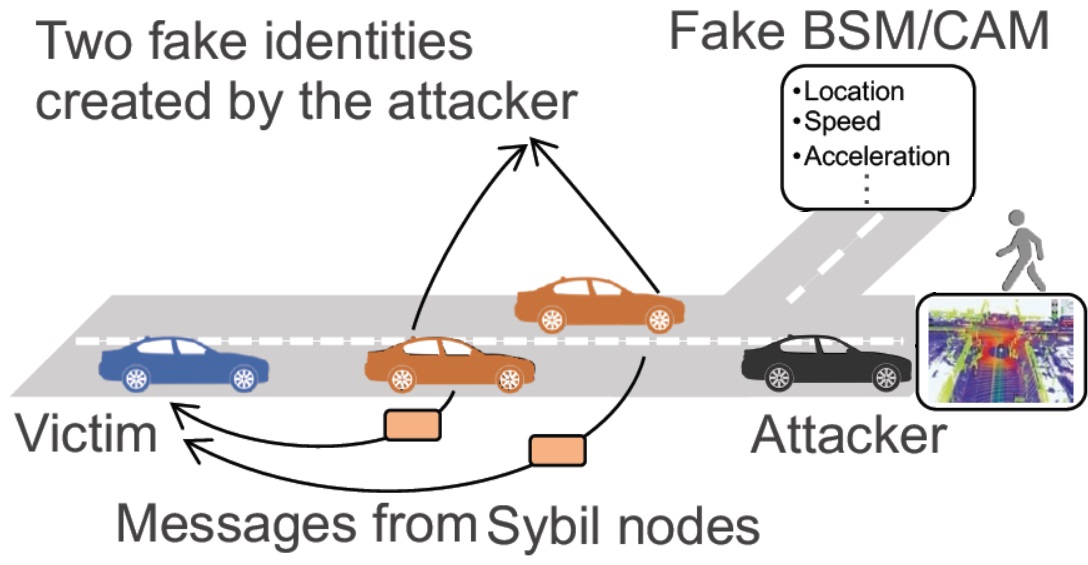
Vehicle Security covers security issues in Connected Car, Electric Vehicle Charging, V2X, Car Smart Key, etc.
There is a potential risk to automotive security from cyber criminals. Security breaches can result in leaked personal data, threats to a vehicle's essential security and safety mechanisms and, in extreme cases, full remote control of the car.
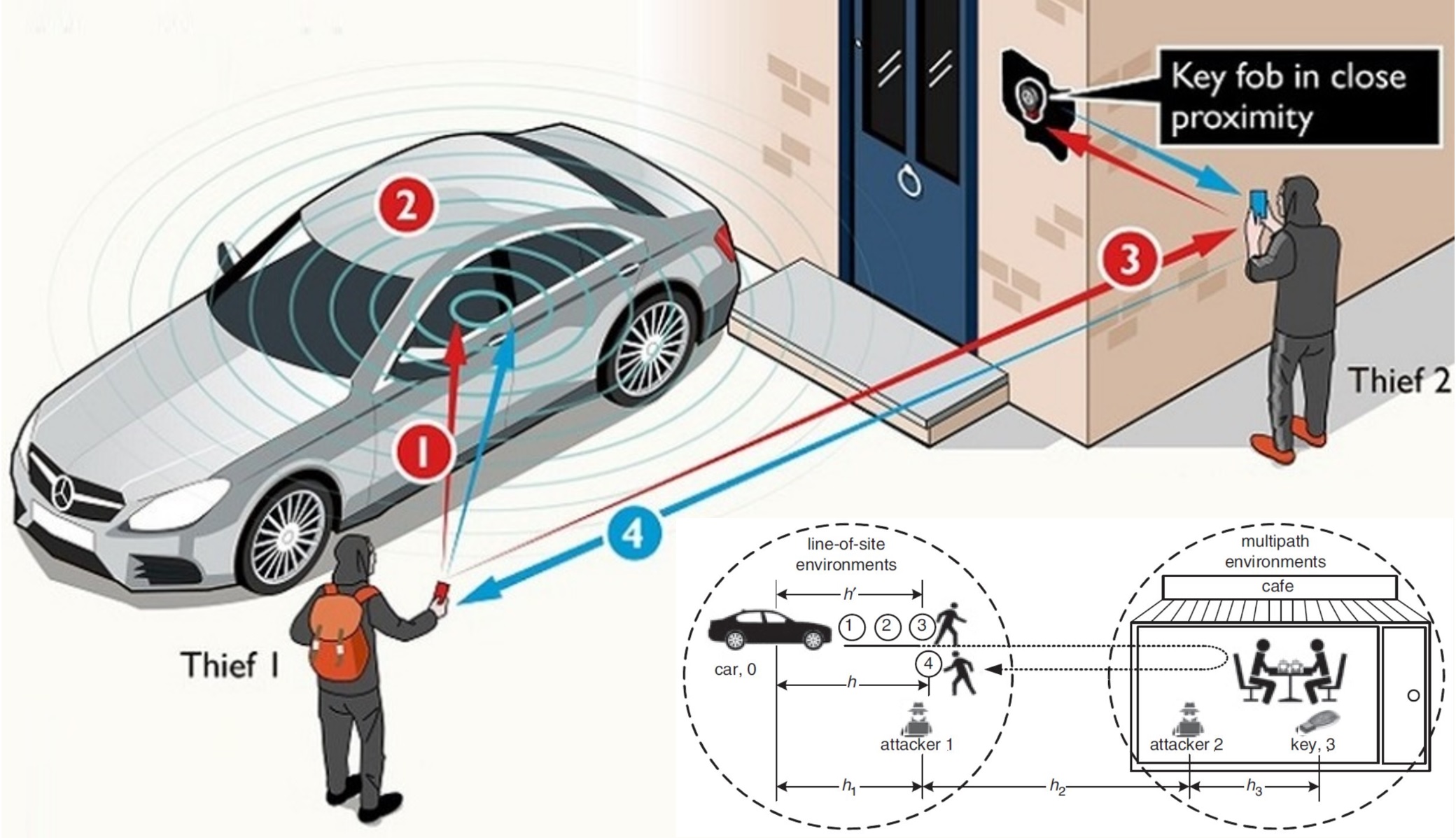
Moreover, passive keyless entry and start (PKES) systems unlocks or starts the car when the key is in the proximity of the car. However, the conventional schemes are vulnerable to relay attacks.
Blockchain and Cryptanalysis:
Blockchain is a shared immutable ledger for recording the history of transactions.
The blockchain isn't really as secure as we tend to think. For example, in the reward of the Bitcoin system, rogue miners can increase their rewards by using the block witholding attacks.
Recently, the cryptanalysis uses the machine-learning technologies to find the characteristics of block ciphers; or to classify encrypted traffic or to identify the cryptographic algorithm from ciphertexts.
 |
 |
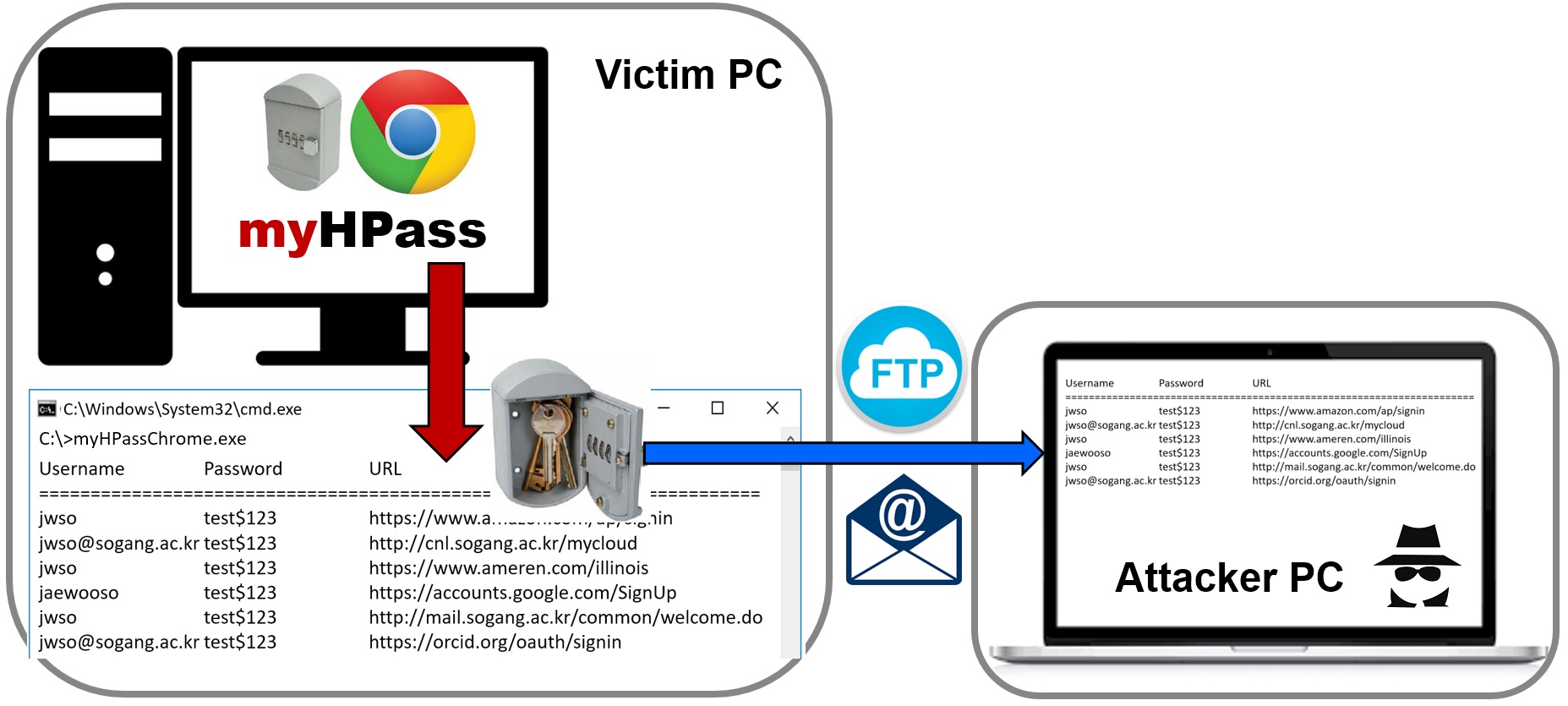 |
| Attacks scenarios of V2X with malicious and victim vehicles | Relay attack avoidance in smart key developed by CNL | Chrome password decryptor developed by CNL |
#